What is a Computer Security Threat?
A computer security threat may be defined as any action or event that may cause damage to any part of a computer system.
 |
| Computer System Security Threats |
How Does Computer Security Threat Cause Damage?
A Computer security threat may cause damage to hardware, software, data , information or processing capability of a computer system.
Hacker is a person who uses computer system to access private data of illegally. Hackers access a computer network and its resources illegally.
Hackers have a vast knowledge of computer science and are computer experts. They may have deep knowledge of high level programming languages, low level programming language, operating systems, computer networks etc. But the problem is that they use their knowledge of computer science and computer systems for negative purpose. This purpose may be financial crimes through hacking online bank accounts or credit cards accounts of online users. Sometimes the purpose is only to annoy people or friends by hacking their social media accounts like face book accounts or twitter accounts. Sometimes hackers may hack email accounts also.
permission or without knowledge of the affected user. Computer viruses are the most common security threat to computer systems all over the world.
Normally a virus will attach itself to a file. When the user executes this infected file, the virus is activated and create disturbance for the computer system working and for the user as well.
Moreover, when we transfer files from the infected flash drives, CDs, DVDs or portable hard drives, the virus is spread into other computer systems and networks.
MyDoom
AntiExe
Blaster
I LOVE YOU
These scams can use websites to attract you into contacting fake technical support people. Online users may be redirected to these websites automatically because of nasty ads found in doubtful sites. These fake websites may be some sites providing fake installers of pirated software, movies or games with serial numbers or hacked setups.
Ransomware can restrict access to data by encrypting files. Sometimes, it may lock the computer screen for this purpose. It then attempts to obtain money by threat from victims by asking for "ransom". The demand of the money is usually in form of crypt-currencies like Bitcoin.
Ransomware demand money in exchange for restoring access to encrypted data of the victim user.
Unwanted software are programs that may change your Operating system experience like Windows settings etc. without your knowledge or permission.
For example unwanted software when installed automatically as a side effect of installing some other software you just downloaded and installed from an authentic website, will change your browser settings. One example of change of browser setting is to change the default page or default search engine setting of the web browser. Moreover unwanted software may show ads that cannot be closed easily. A Potentially Unwanted Program, also called in short as PUP. PUP is a software that contains adware, installs toolbars or has other unclear objectives.
You must always download software from trusted websites. Install freeware carefully. Normally malicious freeware will ask your permission to install some other software too in default setup settings. Read carefully the instructions about license and cancel any new installations.
Different Types of Computer System Security Threat
There are many different types of security threats to computer systems as follows:- Hacker
- Virus
- Worm
- Adware
- Tech support scams
- Ransomware
- PUP Potentially Unwanted Software
Hacker
Hacker is a person who uses computer system to access private data of illegally. Hackers access a computer network and its resources illegally.
 | |
| Hacker - Security Threats To Computer Systems and Networks |
Hackers have a vast knowledge of computer science and are computer experts. They may have deep knowledge of high level programming languages, low level programming language, operating systems, computer networks etc. But the problem is that they use their knowledge of computer science and computer systems for negative purpose. This purpose may be financial crimes through hacking online bank accounts or credit cards accounts of online users. Sometimes the purpose is only to annoy people or friends by hacking their social media accounts like face book accounts or twitter accounts. Sometimes hackers may hack email accounts also.
Some Problems Caused by Hackers
- Hackers may steal the credit card numbers and other details for illegal use and can cause a lot of financial loss.
- Hackers may hack the email accounts of people to use without the knowledge of their users.
- Hackers try to access passwords so that they can access computer systems and intrude in the private networks illegally.
- Hackers may steal private data and information of people through their computer system hack for black mailing purposes.
Virus
Computer Virus is a piece of code that can disturb the normal working of a computer system withoutpermission or without knowledge of the affected user. Computer viruses are the most common security threat to computer systems all over the world.
 |
| Computer Virus- Security Threat To Computer System |
Normally a virus will attach itself to a file. When the user executes this infected file, the virus is activated and create disturbance for the computer system working and for the user as well.
Moreover, when we transfer files from the infected flash drives, CDs, DVDs or portable hard drives, the virus is spread into other computer systems and networks.
Examples of Computer Virus
MyDoom
AntiExe
Blaster
I LOVE YOU
Problems Caused by Computer Virus
Viruses can:- damage the files stored on infected computer systems
- affect the normal working process of computer systems
- delete data stored on disk storage
- display unusual messages that annoy the user and disturb the normal working of the computer. These messages are shown on screen as alerts and user has to close that message dialog box before continue to his/her work.
Worms
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. A worm copies itself repeatedly in memory or on disk until there left no space. This enforces a computer to stop working. |
| Computer Worm-Security Threats To Computer Systems |
Difference Between a Virus and Worm
Often, it uses a computer network to spread itself. Unlike a computer virus, it does not need to attach itself to an existing program. Worms typically cause harm to their host networks by consuming bandwidth and overloading web servers. Whereas viruses almost always corrupt or modify files on a targeted computer.Examples of Worms
- Melissa
- SQL Slammer
- Sasser
- The Blaster
Problems Caused by Worm
- Slow down the computer system by consuming available memory
- Stop the computer working
- Some applications may stop working
- Destroy the files stored on infected computer systems
Adware
Adware is a malicious code designed to display advertisements on your computer. Adware may redirect your search requests to advertising websites to collect marketing data about you, too. The advertisements are shown in popup windows without permission of the user. Adware can keep a record of the user activities on internet to guess his interests, then Adware program will show the advertisements according to the interests of the user.
 |
| Adware - Security Threats To Computer System |
Tech Support System Scams
Tech support scams use scare strategy to trick you into getting help from some fake online technical support people to help you remove fake errors in your system. They demand you for paying for unnecessary technical support services. These fake services may apparently fix a device of your computer system, an operating system defect or some other software errors.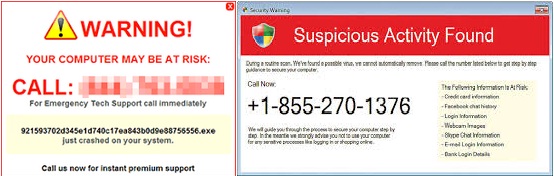 |
| Technical Support SCAM - Security Threat To Computer Systems |
These scams can use websites to attract you into contacting fake technical support people. Online users may be redirected to these websites automatically because of nasty ads found in doubtful sites. These fake websites may be some sites providing fake installers of pirated software, movies or games with serial numbers or hacked setups.
Ransomware
Ransomware can restrict access to data by encrypting files. Sometimes, it may lock the computer screen for this purpose. It then attempts to obtain money by threat from victims by asking for "ransom". The demand of the money is usually in form of crypt-currencies like Bitcoin.
 |
| CryptoLocker Ransomware Security Threat to Computer Systems |
Unwanted software
Unwanted software are programs that may change your Operating system experience like Windows settings etc. without your knowledge or permission.
For example unwanted software when installed automatically as a side effect of installing some other software you just downloaded and installed from an authentic website, will change your browser settings. One example of change of browser setting is to change the default page or default search engine setting of the web browser. Moreover unwanted software may show ads that cannot be closed easily. A Potentially Unwanted Program, also called in short as PUP. PUP is a software that contains adware, installs toolbars or has other unclear objectives.
You must always download software from trusted websites. Install freeware carefully. Normally malicious freeware will ask your permission to install some other software too in default setup settings. Read carefully the instructions about license and cancel any new installations.
Comments